
Chapter 16
The cafe: a case study
The Interaction of cafes and tables
It might seem that the cafe owner would be in an advantaged position. It may be hard to see why anyone would want to sit in somebody else's cafe and help them out with their problems. It is only when you realise that anyone in a cafe can have their own cafe´ that it begins to make sense. Figure 16.11 shows how a table in a cafe might consist of a table of cafe owners. A little bit of mental manipulation lets you understand that the cafes are fixed but that table might be in any one of the owners' cafes.
It makes a great deal of sense for anyone setting up a cafe of collaborators to encourage the people in their cafe to form a cafe of their own. This multiplies the value of each collaborator and makes it easier to exchange favours on a tit for tat basis, i.e., "You sit in my cafe to help me solve my problems and I'll sit in your cafe to help you solve yours".
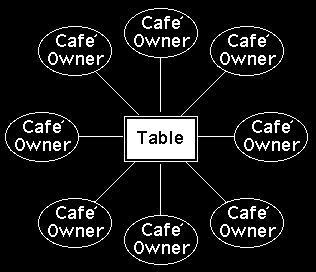
Figure 16.11
People in a cafe can be cafe owners themselves. This would mean a table could be made up of cafe owners who could each call of the expertise within there own cafes to help solve a problem at the table. It would also be possible for people to move in and out of each other's tables on a tit for tat basis
Once you start to think about cafe owners moving in an out of each other's cafes, the boundaries of the cafe´s start to merge. Instead of each cafe´ being a closed network of communication, they become part of a larger whole where information can flow from any table in one cafe to any other table in another.
This is illustrated in figure 16.12, where people having an e-mail discussion at one table are also having an email discussion at another - perhaps in different cafes. Other tables can be linked indirectly to this central table by any of the people in the network taking part in a discussion at a table in another cafe outside of the network. Figure 16.12 shows how a table outside of a communication network of directly connected tables can have two independent links to it through two people being connected to both.
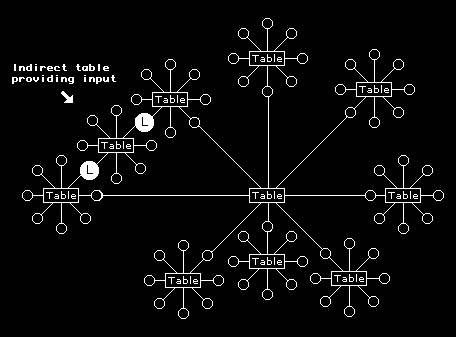
Figure 16.12
Tables in different cafes can be linked by people being part of more than one table discussion. Information arising at any one table can be passed on to any of the others. Because such linking can extend beyond table boundaries the system of communication is open rather than closed
The transparency of cafe boundaries as information flows from one table to another is due to the small-world cluster effect. This is illustrated in in figure 16.13 where person 'A' might have several communication paths that can filter through some important information that person 'B' brings to a table quite remote from person 'A'. Person 'A' is then able to introduce this important information brought up at a remote table by person 'B' to their own table.
This is the power of the Internet, to rapidly disseminate any important information rapidly through a community. A good or bad report on a product or service can flow around the world going from one group to another in a matter of hours.
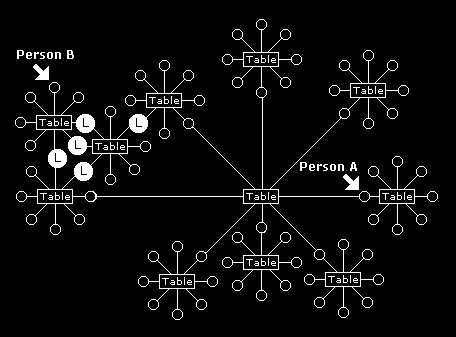
Figure 16.13
An important piece of information, announced by person 'B' at one table discussion group, can rapidly transfer to a remote person 'A' via several other discussion groups at other tables
Not everyone is good at transferring information from one discussion group to another. Sometimes this is deliberate. It is quite common within large companies for people to build power bases for themselves by withholding information. This can be done if there is a hierarchical system of management where information flows from top to bottom. Anyone imposing a block in the flow of information in such a hierarchical system can give themselves a distinct advantage over anyone below them in the chain. Communication by way of e-mail discussion groups can easily by-pass information blockers as illustrated in figure 16.14.
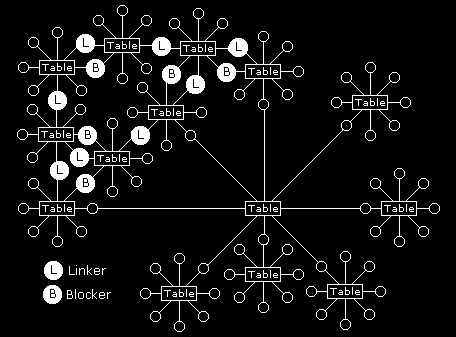
Figure 16.14
With people being able to take part in more than one discussion group it is very hard for anyone to block information flow. Whether blocking is through poor communication or deliberate intent, there are usually many different ways these blocks might be circumvented. How many ways routes can you find around this network to avoid blockers?