
Virtual cafes
by Peter Small
The idea of constructing a virtual cafe came about as a result of trying to extract useful information from the gargantuan mountain of knowledge represented by the Internet and the Web.
I'd likened this ever expanding mountain of knowledge to a vast library, where all the books were randomly placed on shelves and the librarians couldn't keep up with sorting and classifying all the new books that were coming in each day. In such a scenario, it would be a hopeless task to go into this library to try to find a specific piece of information. A more sensible strategy would be to go into the library cafe´ to see if there was anyone in there who'd come across the information that was wanted.
The Internet represented such a cafe´. It contained millions of people who had been routing around in various parts of the Web looking for information. If there was any particular knowledge that needed to be known, there was a fair chance one of them would have come across it. The trick was to find out which one. Such a task would require a Game Theory strategy rather than a logical planned approach. I needed to create software that would help me deal with those millions and find just those who would be able to help me when I needed any particular information.
I started by creating an on screen representation of the cafe´ that would be of a more manageable size. I knew I couldn't list everyone on the Internet, but, I could list all the people I knew. Looking at my email address book, I found this numbered around 500 people. These included close personal friends and many people whom I'd had regular email dialogue with. Mostly though, the names and email addresses were of people I'd corresponded with briefly as a result of my email discussion group activity and book writing.
As I glanced through the list of 500 names, I realised that I couldn't remember much more than a tenth of the people listed. Some names rang a bell, but, I had no idea in what context I'd had correspondence with them and couldn't place who they were. All I was aware of was that they came from all parts of the world and they represented a vast range of different speciality knowledge.
Selecting only those that I could remember who they were, I ended up with a list of about fifty people. As I went over this list, it struck me that these fifty were probably a random sampling of the total list of 500. Statistically, these 50 would represent pretty much the same characteristics as the whole list: people from all over the world with a vast range of different speciality knowledge. Most likely they would have lists of contacts and associates similar to mine. I then realised that being in contact with fifty people was probably just as effective as being in contact with 500. This would allow me to create a cafe of a more manageable size.
This can be appreciated by seeing the situation in terms of the small-world cluster effect. The fifty would probably be in contact with fifty others themselves, this meant that I was within two links of 2,500 people. These would be directly linked to 625,000 others. I soon realised that through a small cafe of fifty people I'd have indirect access to thousands.
This led to a design of a cafe consisting of a main list of five hundred people, with 'seats' in the cafe for a specially selected fifty: those whom I was in more regular contact with. A schematic of the cafe´ software I created is shown in figure 1.
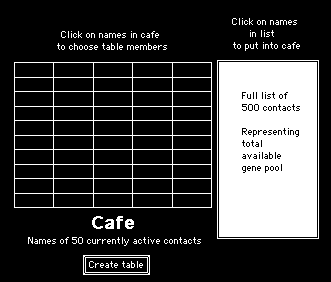
Figure 1 - Schematic of cafe software showing a list of five hundred casual contacts and a method of selecting from these to put some of them into the cafe. Any of those in the cafe can be selected, singly of as a group, to sit at a table for discussion
In the book "Magical A-Life Avatars", I'd expanded on this basic cafe´ model to include software that would allow people to represent themselves as clones. The idea was that people could exchange these clones with acquaintances and contacts so they could appear in each others cafe´s. The clones were created by means of a simple questionnaire that asked various pertinent questions about career and range of knowledge and interests. By making use of these clones – reading in the information they contained and attaching it to the name in the cafe´'s database – cafe´ owners wouldn't have the problem of forgetting the relevant details of the many people they corresponded with on the Internet.
After I wrote the book, I invited all the people in my list of contacts to take part in an on-line discussion forum to explore the possibility of putting these ideas into practice. Unfortunately, it didn't work out as intended. Everyone wanted to approach the project in a different way and instead of a cooperative project, it developed into heated exchanges with the email correspondence descending into disorganised chaos.
To cope with this problem, I used the cafe´ software and put all the people who were subscribed to the discussion forum (again about 500 people) into the cafe´'s database. I then selected from this list the fifty most active posters to place in the cafe´. From these, I could selectively choose small groups to make it possible to have more productive email discussions.
I mentally visualised this as a cafe with tables, where I could select people to join me at a table for a private discussion. This might be one person, two, three or more – about eight participants seemed to be the optimum number for a manageable discussion. The cafe´ selection technique for choosing seven people to join me at a virtual table is illustrated in figure 2.
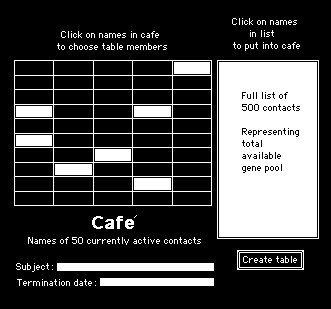
Figure 2 - The screen of a cafe with seven people being selected from a cafe of fifty people to have a private discussion around a virtual table
Selecting a group of people for discussion, was then arranged simply by clicking on the names, which would be highlighted when selected. I arranged for a subject line to describe the nature of the discussion and a termination date to set the length of the discussion. The table could then be created by clicking on the "Create Table" button.
When the "Create Table" button was clicked, the program would then take all the names selected, together with the content of the subject line and the termination date, and create a text file as shown in figure 3.
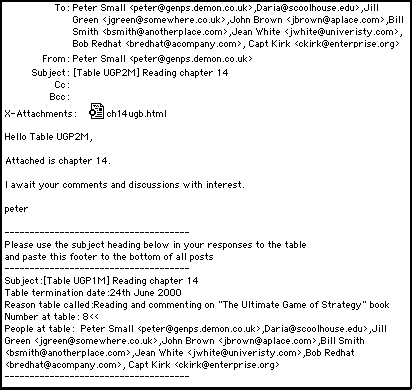
Figure 3 - Example of the text file created when the "Create Table" button is clicked
The table record was stored in such a way that it could be recalled at any time by clicking on a table number and the table details (similar to those shown in 3) would be put into the computer's clipboard ready for pasting into an email.
These table details could then be used as the footer to any email messages sent to the people listed as being at the table. The names could be entered into the "To:" line of the email, so that everyone at the table would receive a copy. The subject line would be entered in and, as every subject line contained a unique name for the created table (in the example this is "[UGP2M]), correspondences from different tables wouldn't get mixed up.
When everyone received a copy of the email, they'd know that to reply to the table they'd have to copy the subject heading and the names from the footer into the "To:" line of their email. In this way each table resulted in the creation of a mini e-mail discussion forum with everyone sending in their responses to the same small group of people. A typical table email is illustrated in figure 4.
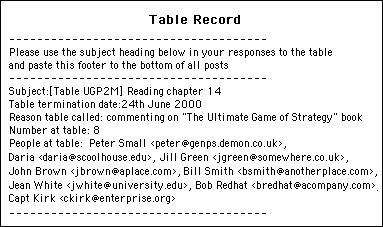
Figure 4 - Email showing how cafe details are entered as a footer. Names are put into the "To:" heading and the identifiable subject line copied in
The cafe proved to be extremely versatile. It could be used to select single names as with regular one to one email dialogues or any number of people selected according to the subject area. The different kinds of table that can be created are shown in figure 5.
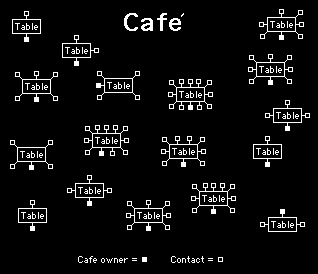
Figure 5 - Different types of table that can be created in the cafe. In this diagram showing how the tables can be made up from a selection of 1 to 12 people (it can go up to 50 but the efficiency starts to go down over 12). All these table can be running simultaneously
The unique advantage of email discussions over real life discussions, chat lines or tele-conferencing, is that it is possible to take part in many discussions simultaneously. In the context of the cafe´, it means that the cafe owner can create several tables and sit at all of them at the same time. This is illustrated in figure 6.
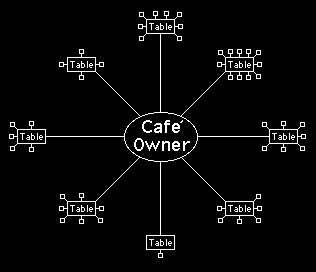
Figure 6 - The owner of a cafe can create several tables for different discussions and sit at them all at the same time
One of the many advantages of being able to hold simultaneous discussions in different on-line discussion forums is that ideas can be developed by moving them around to different tables. This is illustrated in figure 7.
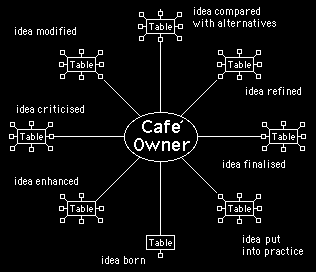
Figure 7 - A cafe owner can move ideas around to different tables, to get various different opinions and view points. With the right groups of people in the cafe, an idea can be developed from conception to implementation
Suitably choosing different mixes of people at the tables, and switching an idea between tables, the cafe can be used as a sophisticated idea processing device. The idea can be exposed to different groups who might look at it in different ways. Although this may involve only a limited number of people in the cafe, the small-world cluster effect can effectively call upon the knowledge and influence of hundreds.
The cafe can be used with paid advisers or employees sitting at the tables. It can be used amongst peers: experts and specialist, working in the same field, who help each other out with the exchange of information and ideas. Indeed, it can include a mixture of all three, as would often be the case in a real life e-business situation.
Figure 8 shows how an auteur might use a cafe to design e-business solutions. They'd have a direct connection to their main employer, the entrepreneur or client. They have a table to talk jointly with key representatives of the producers of the core product. They'd have tables to discuss marketing, hardware requirements, Web site design, back end data bases, fulfilment and logistics, etc. They'd probably have tables set aside to have discussions with various other people whom they'd know from Internet discussion forums: peers who work on similar problems to themselves.
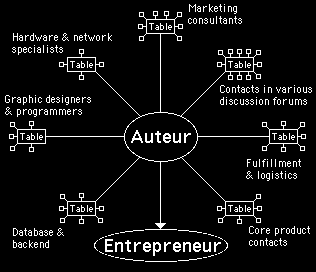
Figure 8 - An auteur, working on an e-business solution, might set up a cafe to organise all the collaborators who are involved in the project
Notice, in figure 8, that none of the collaborators in the auteur's cafe need be employees. Neither need they have to work as a managed team. Some could be paid, others could be contributing on a tit for tat basis. An auteur can call tables into action on a discontinuous basis, for short periods at a time. Also, the auteur can call several table into action concurrently and be able to sit in on all of the discussions at the same time – perhaps swapping information from one table to another where applicable.
Similarly, entrepreneurs might arrange their business organisation through a cafe´. They may have tables to discuss financing with investors, advertising and marketing with consultants, legal matters with lawyers, core product matters with producers. They may take the precaution of using several auteurs to work independently on the same e-business solution, to make sure they do not get locked into an inferior approach. Such an entrepreneur's cafe´ may take the form illustrated in figure 9.
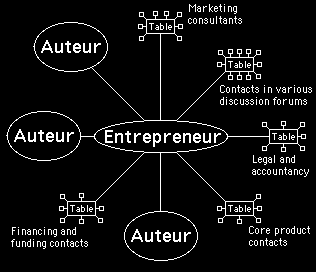
Figure 9 - A cafe set up by an entrepreneur, who covers the risk of getting locked into an inferior solution by using several auteurs to work independently on the same e-business solution
The use of a cafe is not confined to entrepreneurs and auteurs. Any executive working in a conventional business environment could also use the Internet and a cafe´ to organise their functions and responsibilities. Figure 10 illustrates how an executive manager who reports only to the CEO might organise the functioning of his or her responsibilities.
Instead of sitting in on endless rounds of time consuming real life meetings, they could run all meetings concurrently and be able to sit in on them all at the same time without leaving their office. Because of the unique way in which e-mail discussions work, they would not have to wait through hours of inconsequential detail before coming to the crucial issues that need their attention. In the virtual world of e-mail discussion, the most vital aspects can be isolated to be able concentrate attention upon.
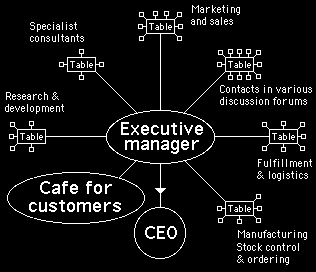
Figure 10 - Cafes can be set up by executives in conventional companies. By means of the Internet, they can monitor and control a variety of different departments and obtain feedback from customers or clients
Notice in figure 10 how the executive manager is shown as having a separate cafe set up to have discussions with customers or clients. This allows them to have a uniquely valuable perspective when they take part in discussions at the various departmental tables.
The CEO might not even be aware of the methods by which the executive manager is organising his functionality through the Internet and a cafe´. It would probably be a mystery as to how everything in the organisation was running so smoothly.
The Interaction of cafes and tables
It might seem that the cafe owner would be in an advantaged position. It may be hard to see why anyone would want to sit in somebody else's cafe and help them out with their problems. It is only when you realise that anyone in a cafe can have their own cafe´ that it begins to make sense. Figure 11 shows how a table in a cafe might consist of a table of cafe owners. A little bit of mental manipulation lets you understand that the cafes are fixed but that table might be in any one of the owners' cafes.
It makes a great deal of sense for anyone setting up a cafe of collaborators to encourage the people in their cafe to form a cafe of their own. This multiplies the value of each collaborator and makes it easier to exchange favours on a tit for tat basis, i.e., "You sit in my cafe to help me solve my problems and I'll sit in your cafe to help you solve yours".
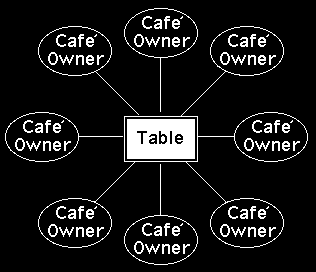
Figure 11 - People in a cafe can be cafe owners themselves. This would mean a table could be made up of cafe owners who could each call of the expertise within there own cafes to help solve a problem at the table. It would also be possible for people to move in and out of each other's tables on a tit for tat basis
Once you start to think about cafe owners moving in an out of each other's cafes, the boundaries of the cafe´s start to merge. Instead of each cafe´ being a closed network of communication, they become part of a larger whole where information can flow from any table in one cafe to any other table in another.
This is illustrated in figure 12, where people having an e-mail discussion at one table are also having an email discussion at another – perhaps in different cafes. Other tables can be linked indirectly to this central table by any of the people in the network taking part in a discussion at a table in another cafe outside of the network. Figure 12 shows how a table outside of a communication network of directly connected tables can have two independent links to it through two people being connected to both.
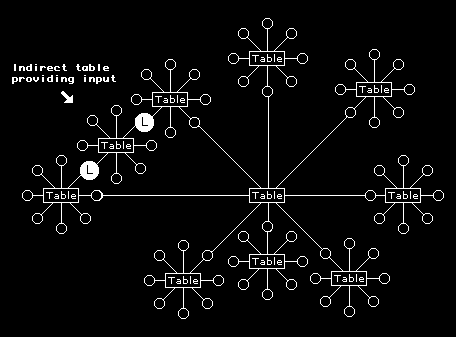
Figure 12 - Tables in different cafes can be linked by people being part of more than one table discussion. Information arising at any one table can be passed on to any of the others. Because such linking can extend beyond table boundaries the system of communication is open rather than closed
The transparency of cafe boundaries as information flows from one table to another is due to the small-world cluster effect. This is illustrated in in figure 13 where person 'A' might have several communication paths that can filter through some important information that person 'B' brings to a table quite remote from person 'A'. Person 'A' is then able to introduce this important information brought up at a remote table by person 'B' to their own table.
This is the power of the Internet, to rapidly disseminate any important information rapidly through a community. A good or bad report on a product or service can flow around the world going from one group to another in a matter of hours.
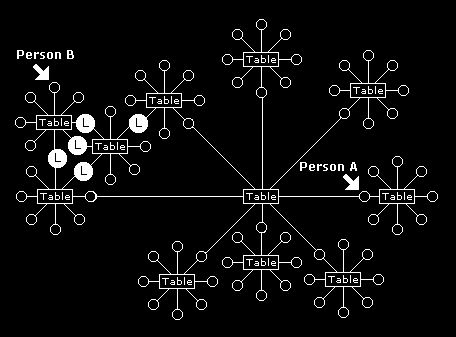
Figure 13 - An important piece of information, announced by person 'B' at one table discussion group, can rapidly transfer to a remote person 'A' via several other discussion groups at other tables
Not everyone is good at transferring information from one discussion group to another. Sometimes this is deliberate. It is quite common within large companies for people to build power bases for themselves by withholding information. This can be done if there is a hierarchical system of management where information flows from top to bottom. Anyone imposing a block in the flow of information in such a hierarchical system can give themselves a distinct advantage over anyone below them in the chain. Communication by way of e-mail discussion groups can easily by-pass information blockers as illustrated in figure 14.
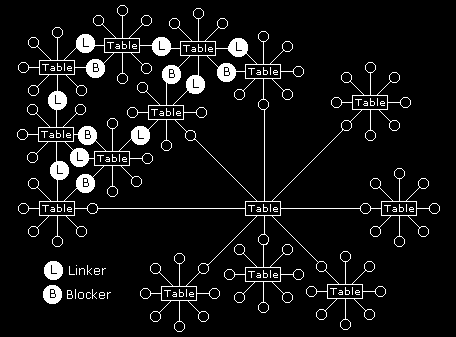
Figure 14 - With people being able to take part in more than one discussion group it is very hard for anyone to block information flow. Whether blocking is through poor communication or deliberate intent, there are usually many different ways these blocks might be circumvented. How many ways routes can you find around this network to avoid blockers?